Data Transfer Pro for Accounting Department
Data transfer for the accounting department is of great importance for the smooth operation and proper management of critical business processes such as the financial management of the business, accounting records and tax returns. Data Transfer Pro uses a special encryption system to secure your data in your accounting department, thus keeping information security at the highest level. These security measures in data transfer allow you to manage your business processes more effectively and reliably.
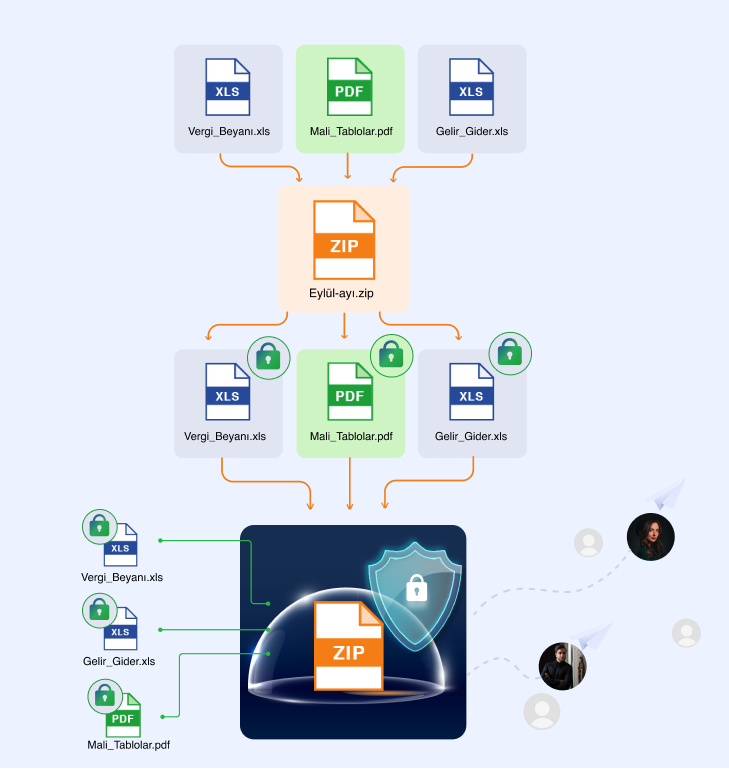
Double-Stage Security and Shipment Tracking
Using double-stage security in all your data transfer transactions ensures that only authorized persons have access to your accounting information. This method creates an additional layer to increase the security of your data. The two-stage security approach helps keep your sensitive financial data safe by providing extra protection against unauthorized access to your accounting information.
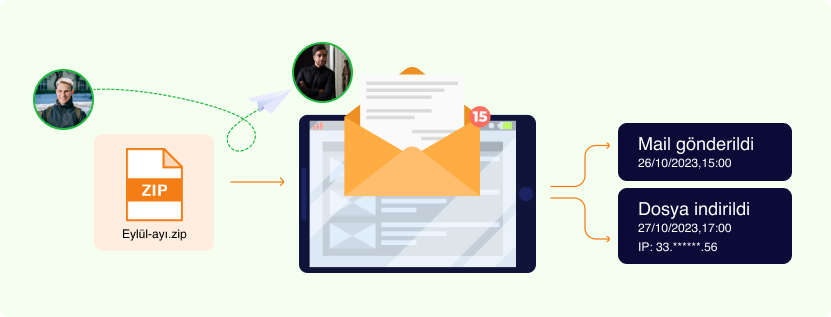
Accounting with Data Transfer Pro: Secure and Fast Data Transfer!
Secure data transfer for accounting departments is directly related to a number of critical issues such as financial accuracy, tax compliance, cost control, investor relations and legal compliance. With Data Transfer Pro, accounting departments transfer data securely, always maintaining the financial stability and reliability of the business, thus increasing your Customer Trust and added value!

Why choose us?


AES 256-bit hardware-based encryption
Thanks to AES 256 encryption, your data is protected by a strong encryption system in all storage, sharing and viewing processes.

Send any type of data you want
Regardless of the file type, you can share all your photos, videos, presentations and reports with recipients.

Create team & address book
In addition to using your address book, you can create groups and contact lists, gaining efficiency for recurring transfers.

Link tracking
You can control the viewing, saving and downloading activity of all your transmissions
Our security protocol

End-to-End Encryption
Wing Transfer uses end-to-end encryption to encrypt user data from beginning to end, preventing the data from being publicly viewed at any stage during transfer.
Key Management
Wing Transfer securely manages encryption keys. This ensures that the keys are protected against unauthorized access and increases the level of security.
Session Based Security
Wing Transfer increases security by creating one-time session keys for each file transfer. This ensures that each transfer is protected with a unique key.
Network Security
Wing Transfer may use VPN (Virtual Private Network) or similar technologies to increase network security during file transfers. This ensures that data is transmitted in a more secure environment during transfer.
Temporary Memory Clearing
After the file transfer is complete, the encryption used keys and temporary memory are automatically cleared from the system. This minimizes security vulnerabilities and eliminates data traces.
Time-Limited Keys
Wing Transfer makes the encryption keys used for file transfer time-limited. This ensures that a key is only valid for a certain period of time which increases security.